Check out how dangerous is Cross Site Request Forgery (CSRF)
Cross Site Request Forgery (CSRF), also referred to as XSRF, Sea Surf, or Session Riding is an attack that forces authenticated customers
to send a request to an internet application that they’re presently authenticated against. With a bit of help from social engineering,
an attacker can trick customers of a web software into appearing whatever moves they want.
Cross site Request Forgery is considered a sleeping giant in the web application security world.
A successful CSRF attack may be devastating for both the enterprise and the user. This can cause harm to client relationships,
unauthorized fund transfers changed passwords, and statistics theft, including stolen session cookies.
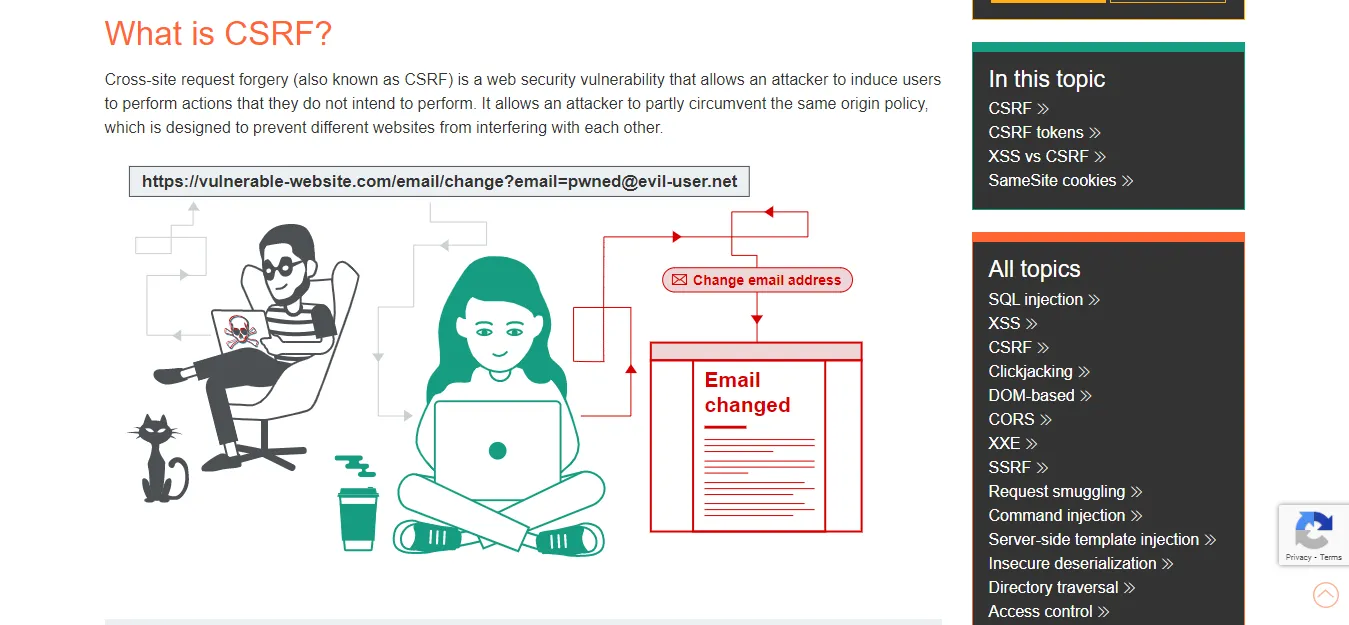
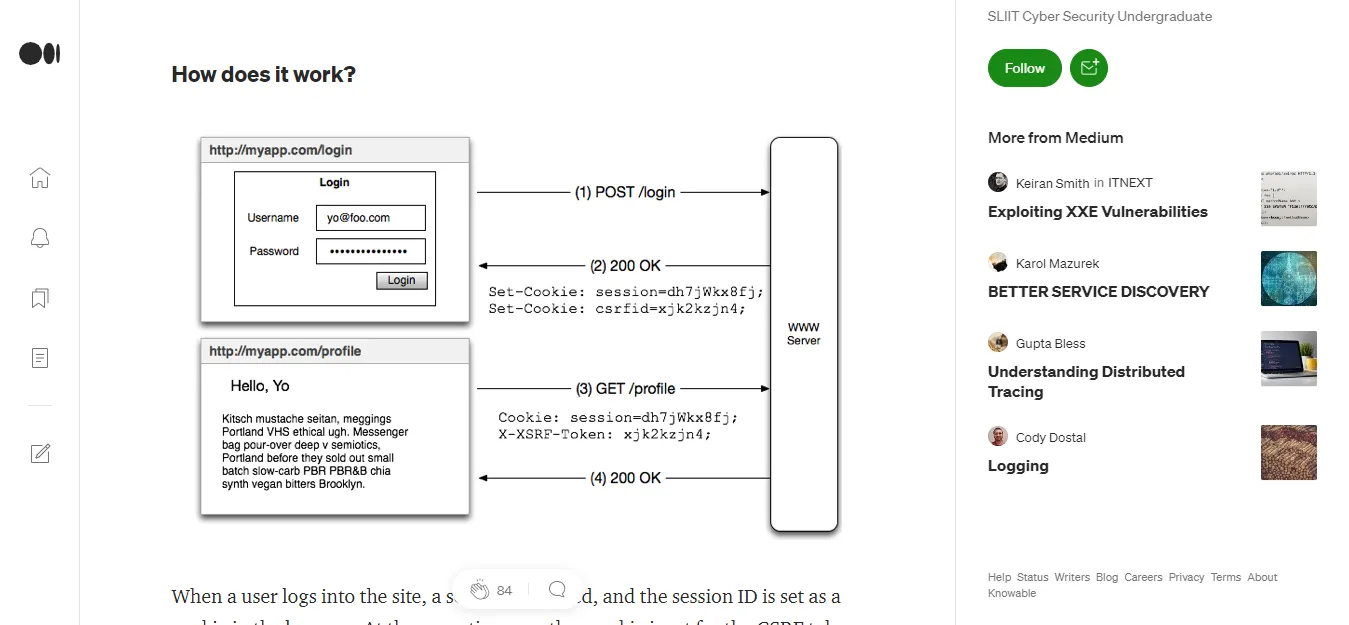
How Are Cross Site Request Forgery (CSRF) Attacks Executed
For a CSRF attack to be possible, three key conditions must be present:
Relevant action. There is an action within the application that the attacker has reason to induce.
This can be a privileged action such as changing permissions for other users or any action on user-specific data such as changing the user’s password.
Session management based on cookies. Completing the action involves issuing one or more HTTP requests, and the application relies only
on session cookies to identify the user who made the requests. There are no other mechanisms available to track sessions or validate user requests.
No unpredictable query parameters. The queries that act do not contain any parameters whose values the attacker cannot determine or guess.
For example, when it prompts a user to change their password, the function is not vulnerable if an attacker needs to know the value of the existing password.
If these conditions are true, the attacking side triggers an HTTP request to the vulnerable website. If the user is logged into the vulnerable website,
the browser will automatically include the session cookie in the request (assuming cookies from the same site are not used).
The vulnerable website processes the request normally, treating it as if it had been made by the user’s victim and changing their email address.
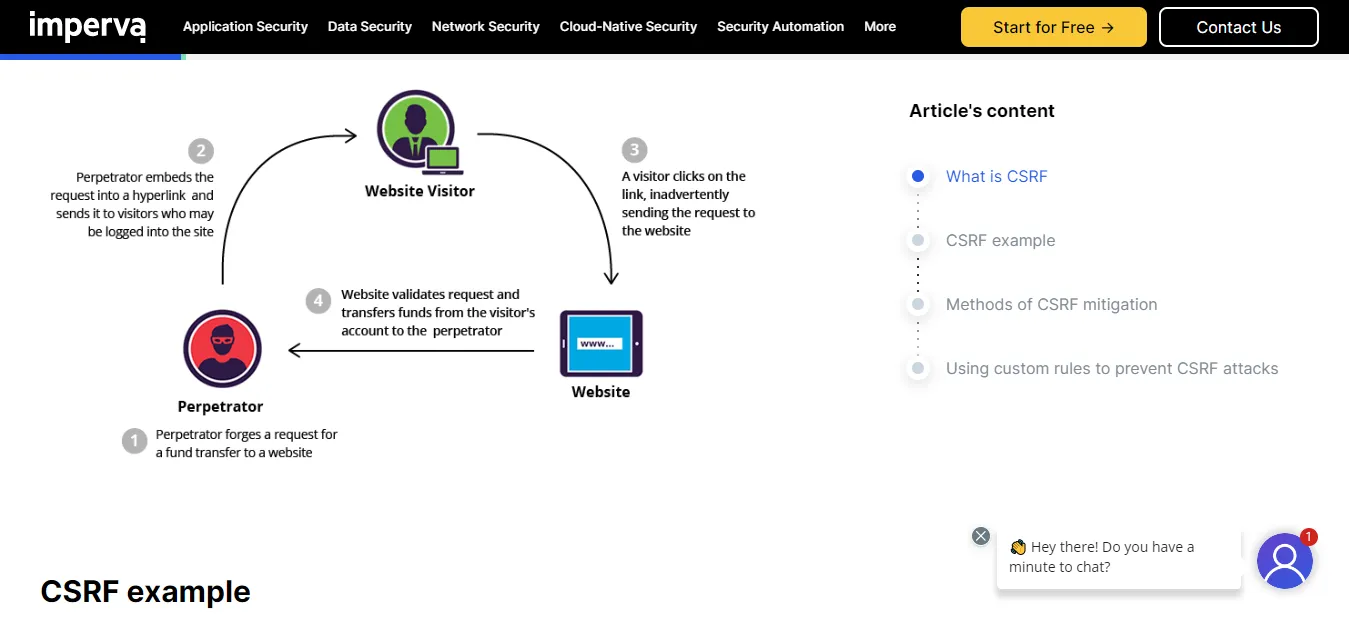
How to Prevent Cross Site Request Forgery Attacks
Using Anti-CSRF Token
An anti-CSRF token is a type of server-side CSRF security. This is a random string of characters known only to the user’s browser and web application.
The anti-CSRF token is generally stored in a session variable. the field submitted with the request.
If the values of the session variable and the hidden form field match, the web application accepts the request; if they do not match, the request is canceled;
In this case, the attacker does not know the exact value of the hidden form field that is required to accept the request, so that he cannot launch a Cross Site Request Forgery (CSRF) attack.
Set cookies with the Same Site Attribute
The Same site cookie method limits the start from which a cookie can be sent, so CSRF uses the ability to generate a cross-origin request and ultimately cookies from the same website.

Double-submit cookie prevention
If a valid token cannot be used on the server-side, a double-send cookie token approach can be used on the user’s device, in addition to the cookie that serves as the session identifier.
If a valid request is sent to the site, it must include the same rate found in the cookie. The server then checks it and if the values match, the request parameter is accepted.
Requiring additional authentication for sensitive actions
Before performing critical and sensitive actions on your site, it is always a good idea to ask users to re-authenticate.
This may be an OTP sent to a registered e-mail address or phone number, a simple CAPTCHA, or a password renewal,
prevents any form of Cross Site Request Forgery (CSRF) attack and probable more dangerous attacks.

Check out our latest blog on why WordPress is popular CMS.









Comments